Hello there! Daniel here with another digest 💌
This week, we went to KubeCon Europe in Paris and were pleasantly surprised at how big of a thing fine-grained authorization is becoming.
We ourselves gave two talks about authorization and policy as code (but that’s no surprise - we’re biased):
Raz Cohen talked about Policy as Code: A Game-Changer for Stack Security, and how the friction between developers and security is breaking thanks to better developer experiences.
Gabriel L. Manor shared his insight about Love, Hate, and Policy Languages.
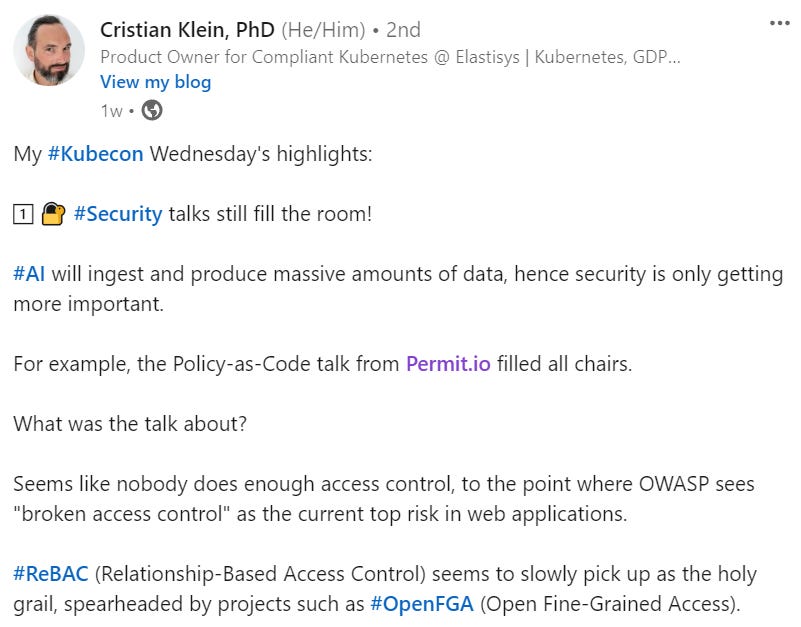
But don't take it from us (again, we are biased), here’s what Cristian Klein had to say -
Even though trends are a common thing in the developer community, they often focus on useless solutions that have a buzz around them (Did somebody say Web3?).

Authorization is a whole different story, though. There are a few reasons (Which Gabriel outlined in his talk) why authorization is gradually generating more and more interest -
Cloud-native architecture creates a new need to streamline policy decisions across the whole stack, with a single common configuration layer and a single source of truth for decisions.
The data we're processing is growing exponentially every day, and with it the amount of authorization decisions we need to make. ‘Decision fatigue’ is becoming more and more common in teams who deal with tons of data (And those trying to pick where to order food from).
The velocity required when deploying applications also creates lots of friction for security features, and access control is the first thing you want to prevent from breaking.
Users require more control of their data, its ownership and privacy. This results in fine-grained authorization being a basic requirement in an ever-increasing number of applications.
With these reasons in mind, it wasn’t a surprise to see as many people talk about the subject of authorization. Gabriel then proceeded to share trends in policy languages and our own open-source project, OPAL, which allows you to manage policy-as-code and policy-as-graph in scale.
One of the most exciting things about Policy as Code and authorization engines is to see how they break the barriers between different layers of the stack. This doesn’t only mean making Product, Data, DevOps, and Security engineers better friends (God knows they need that) but also creating new opportunities for platform engineering teams to deliver faster and better results.
In their amazing keynote, Leon and Yuhzui from Bloomberg told us their fascinating end-user story about the machine learning platform they creatively designed based solely on various CNCF projects. We also love hearing Yao and Yifan’s deep dive into using Istio and OPA, proving once more that the product stack and security can coexist in peace.
Andres Aguiar gave a great talk about Fine Grained Authorization with OpenFGA - it was super exciting to hear Ubuntu is going to use OpenFGA as their authorization engine in the next Ubuntu server release.
In other exciting OpenFGA infrastructure news (Yes, that’s a thing now), Jonathan Whitaker from Okta shared an amazing workflow for controlling K8S admissions with OpenFGA. The admission space is growing, and it's great to see an application-oriented engine join the party.
Anders (A reoccurring theme, it seems) Eknert, and Peter Macdonald from OPA shared an exciting use case of enforcing policies for Backstage, showing how we can give developers the fine-grained permissions and better experiences they deserve. We also loved his OPA deep dive talk, and we recommend giving it a watch if you haven’t yet.
To wrap up, the folks from Keycloak, Takashi and Thomas, delivered a great talk about the space between AuthN and AuthZ. We really believe Keycloak could be a great addition to any fine-grained authorization policy engine, and it’s awesome to see this project continue to grow.
Speaking of platform engineering and policy as code, Or, our CEO, just wrote some of his thoughts on policy-as-code as the key to a successful platform engineering experience. Check it out!
It’s more than amazing to see this space displaying such rapid growth. We cannot wait to see all of these amazing policy engines grow (OPA/OpenFGA/Cedar), and, aiming to be completely policy engine agnostic, provide great user experiences for all Permit users on top of them.
As always, it’s been a pleasure, and I hope to see you in our Slack Community!
See you in two weeks!
Daniel ❤️